Your walking to work and you reach into your pocket retrieving a small device not much bigger than a cell phone. Its flexible and transparent much like the inner window of an airplane. The device sits perfectly in your hand. You notice how well the little weight it has balances in your palm without gripping the device. You remember dropping it yesterday causing a noticeable abrasion on the screen but today there doesn't appear to be any damage. As you slide the device open with your thumb, a 3 dimensional display unfolds like a fan from the center of the screen. It hovers at a 30 degree angle just an inch or so below your thumb. In the center is an enticing illuminated floating orb. It resembles your favorite piece of fruit. You peel away a section of its outer layer revealing an item called "Transit tool". You lift the device just above head level centering the transparent panel on a sign marked "Transit assist". The device recognizes what bus your waiting for then says to you "the 15 downtown will arrive in 7min". There are several other buttons situated along this display just below the orb; their purpose changing as you peel away different sections of the orb. The functionality in each layer comprises everything from entertainment and recreation to safety and self enrichment. You marvel at the fact that you could schedule a doctors appointment, pay for a candy bar without going to the register, and run a diagnostic check on your car's fluids and tires in a matter of seconds with just a few flicks of your thumb.
After a short bus ride you arrive at your desk and place your device in a dock. The orb grows legs and arms, waves good bye, and hops off the device disseminating in a burst of white particles. You do a 180 in your chair to face a rather large surreal holographic image of a Dali painting in motion. The small glowing orb in cartoon like fashion leaps into view and the painting slowly fades away. After a moment of jazz hands (and a rather adorable "tada!") the orb (whom you've affectionately named Harry) retracts its little arms and legs returning to an inanimate state awaiting its next instruction.
It sounds like the works of science fiction but the technologies I describe here are very real, and in the not so far off future, will reinvent the computers we live and work with. Breakthroughs in Nanoscience, cloud computing, and even Holographics! are bringing some exciting changes to hardware components, software environments, and overall sex appeal of consumer electronics. By the end of the next 2 decades we may witness the death of the desktop PC; a device that is relatively unchanged in appearance for the last 15 years.
Nanoscience, a field of study credited for such innovations as self-repairing materials, nano storage, and carbon nanotubes, is giving engineers new frontiers to explore for product design. Scientists are already racing to replace silicon components with ultra-light, incredibly strong, and highly conductive materials. Materials produced from nanotechnology are perfect replacements for silicon based circuit boards. Graphene, a nobel prize winning material revolutionizes the 3 proponents for computing: data storage, transistors, and energy storage. Imagine computers so small they could fit into your contact lenses or on the head of a pin.
Cloud computing will one day allow people like you and me to run Mac, windows, Linux, your tivo, your microwave, your car, your tooth brush, and flush your toilet all from one device. A good way to think of the "cloud of the future" is to imagine web pages you visit as fully functional desktop PC's. Each web page is a customizable computer with all the processing power several of todays computers. You have access to thousands of application and and software environments all through a device the size of an iPhone. With a combination of a technique called Virtualization and the cloud, displaying and submitting information are the only roles your computer is tasked with. The processing, storage, and handling of said information will be performed over an internet connection; stored in a dust free, super cooled, climate controlled data warehouse hundreds of miles away. The cloud will remove the need for many of the physical and software components that burden people like you an me with things like component damage, Operating system failure, and Virus infection.
Putting the final nail in the desktop PC coffin is Interactive Holographics. Interactive Holographics is the next big frontier interactivity and perhaps the biggest technological challenge faced by engineers today. A group of researchers from the University of Arizona have announced a recent project allowing holographic images to be quickly written and rewritten to a single digital medium. Researchers also stated during an interview after the conference that in the next 15 years holographic televisions for the general public are a feasible reality. Another recent invention worth mentioning (and more closely related to the device in the introduction) is this lovely piece of touchable holography. Both these beasts are still decades away from true holography but just 5 years ago this wasn't even possible.
Be sure to click the links for more info.
Thursday, November 11, 2010
Saturday, March 6, 2010
Mac Users: Getting around IMovie's limited Video formats
I recently discovered how limited IMovie is concerning video formats. I was shocked to find that one of the most successful movie editing programs for the OS X isn't capable of encoding a video in a very common format that, for example, YouTube requires as a usable video format. To get around this you can do one of two things for a Mac: Shell out $1000.0o for final cut pro, or download a freeware video conversion tool that is very easy to use and, well, free!
So what right?
Something I've never had the need to do but discovered is very effective at acquiring stock video footage, is using YouTube video downloading tools for finding clips of video material that I could splice into my videos. I've recently been tasks as part of a group project with creating a short movie that would spoof an MTV show called Pimp My Ride. As with every video project, time and budget constraints are a big issue and stock footage becomes a viable and, if done right, tasteful option.
Video clips that are not .mov (quicktime), or digital video format files will not work in IMovie. To get my stock footage clips I downloaded to work in Imovie, I used Isquint to encode my video clips in a format IMovie would understand. Although ISquint is a program that has been discontinued and is no longer for sale, its only a couple years old, works well, and is extremely easy to use.
Find several methods of downloading Youtube video here: CNet HowTo Download Youtube Video
Download Isquint here: http://www.versiontracker.com/dyn/moreinfo/macosx/28250
So what right?
Something I've never had the need to do but discovered is very effective at acquiring stock video footage, is using YouTube video downloading tools for finding clips of video material that I could splice into my videos. I've recently been tasks as part of a group project with creating a short movie that would spoof an MTV show called Pimp My Ride. As with every video project, time and budget constraints are a big issue and stock footage becomes a viable and, if done right, tasteful option.
Video clips that are not .mov (quicktime), or digital video format files will not work in IMovie. To get my stock footage clips I downloaded to work in Imovie, I used Isquint to encode my video clips in a format IMovie would understand. Although ISquint is a program that has been discontinued and is no longer for sale, its only a couple years old, works well, and is extremely easy to use.
Find several methods of downloading Youtube video here: CNet HowTo Download Youtube Video
Download Isquint here: http://www.versiontracker.com/dyn/moreinfo/macosx/28250
Wednesday, March 3, 2010
Improve your professional composure with a few tech savy phrases
An increasing number of non-technical related positions are requiring applicants have a familiarity with enterprise wide applications. Small businesses are also look for sharp young professionals adept at staying current with industry trends and innovative new markets. Since moving to the bay area 6 months ago I've been competing with thousands of talented young professionals for positions in Graphic Design, Marketing, Customer Service, Software Development, Tech Support, Food Service, General Laboring, Transportation and just about everything else. A great way I found to stand out in a sea of amazing was to mention a computing concept or two that could potentially save my prospective employer money.
Got an interview with a big company?
A new trend in many industries for rolling out enterprise wide applications is Cloud Computing. In a nutshell, Cloud Computing allows large companies to focus on developing quality applications rather than excessively spending money on equipment and teams of people to support them. The intended purpose of cloud computing was to create ways for employees to access applications securely from anywhere so long as they have an Internet connection. These web based applications have access to company wide resources allowing someone to perform large time consuming tasks efficiently without worry of backed up methods and data security. Currently, companies spend hundreds of thousands of dollars purchasing servers, software, and very expensive engineers. Cloud computing has eliminated the need for a company to locally house data centers.
If your applying for a large company and they ask you about what new ideas you can bring to the table, mention your "experience" with Cloud Computing applications and how much they enhanced the productivity with your previous company. Here is a list of companies providing Cloud Computing resources to companies world wide:
Salesforce.com (CRM)
Google (GOOG)
NetSuite (N)
Taleo (TLEO)
Concur Technologies (CNQR)
Info Technologies (IT)
If you'd like more info on Cloud Computing, you can go to http://www.salesforce.com/cloudcomputing/ for a breakdown and video.
Or here for a great article on new implementations:
http://gizmodo.com/5485804/ballmer-explains-the-cloud-in-5-easy-steps?skyline=true&s=i
Interviewing for a smaller business?
Small businesses are constantly looking for effective and cheap (if not free) ways to advertise their business making them more appealing and noticeable without the need for gimmicks or insane deals. This can often be a very tedious process of trial and error. Late last year I began outlining my own business blueprint and discovered a software category slowly emerging in popularity called Niche Market software.
Let's face it, Google has become a hub for getting information on product and service availability. If you need gardening equipment, perform a google search for gardening stores close by. If you're tired of the same old coffee shop, try something new via google. If your favorite store just moved locations, Gmap it! A business with 100% of their customers on the Internet now faces the challenge of climbing the search results ladder. A difficult task when the results are in the millions.
Niche Market Software helps a business decide how and what market to advertise in with the least amount of competition and highest amount of Google searches. By analyzing search terms related to your business, and the amount of business's that fall under each category, you can tailor your business's web page to use terms that will place your site higher on the Google search list. For instance, if I am setting up a t-shirt company I would probably avoid using search tags like "funny t-shirts" and "custom Tee's" for my website. I will undoubtedly be buried under my search competition. Since Google lists results by highest amount hits, a new business with little or no hits may never see the light of day. By finding a "Niche Market" rich with Googlers, relevant to my business, and little competition, I am sure to give my business the kindling it needs to attack larger markets. Niche Market software has a slew of features that are quite useful for achieving your marketing goals.
So, the next time you're interviewing for a small business, you can mention that Niche Market software was a great way your last manager had his/her marketing team compile data on the competition.
You can find a great piece of Niche Market Software @ http://www.marketsamurai.com/.
Got an interview with a big company?
A new trend in many industries for rolling out enterprise wide applications is Cloud Computing. In a nutshell, Cloud Computing allows large companies to focus on developing quality applications rather than excessively spending money on equipment and teams of people to support them. The intended purpose of cloud computing was to create ways for employees to access applications securely from anywhere so long as they have an Internet connection. These web based applications have access to company wide resources allowing someone to perform large time consuming tasks efficiently without worry of backed up methods and data security. Currently, companies spend hundreds of thousands of dollars purchasing servers, software, and very expensive engineers. Cloud computing has eliminated the need for a company to locally house data centers.
If your applying for a large company and they ask you about what new ideas you can bring to the table, mention your "experience" with Cloud Computing applications and how much they enhanced the productivity with your previous company. Here is a list of companies providing Cloud Computing resources to companies world wide:
Salesforce.com (CRM)
Google (GOOG)
NetSuite (N)
Taleo (TLEO)
Concur Technologies (CNQR)
Info Technologies (IT)
If you'd like more info on Cloud Computing, you can go to http://www.salesforce.com/cloudcomputing/ for a breakdown and video.
Or here for a great article on new implementations:
http://gizmodo.com/5485804/ballmer-explains-the-cloud-in-5-easy-steps?skyline=true&s=i
Interviewing for a smaller business?
Small businesses are constantly looking for effective and cheap (if not free) ways to advertise their business making them more appealing and noticeable without the need for gimmicks or insane deals. This can often be a very tedious process of trial and error. Late last year I began outlining my own business blueprint and discovered a software category slowly emerging in popularity called Niche Market software.
Let's face it, Google has become a hub for getting information on product and service availability. If you need gardening equipment, perform a google search for gardening stores close by. If you're tired of the same old coffee shop, try something new via google. If your favorite store just moved locations, Gmap it! A business with 100% of their customers on the Internet now faces the challenge of climbing the search results ladder. A difficult task when the results are in the millions.
Niche Market Software helps a business decide how and what market to advertise in with the least amount of competition and highest amount of Google searches. By analyzing search terms related to your business, and the amount of business's that fall under each category, you can tailor your business's web page to use terms that will place your site higher on the Google search list. For instance, if I am setting up a t-shirt company I would probably avoid using search tags like "funny t-shirts" and "custom Tee's" for my website. I will undoubtedly be buried under my search competition. Since Google lists results by highest amount hits, a new business with little or no hits may never see the light of day. By finding a "Niche Market" rich with Googlers, relevant to my business, and little competition, I am sure to give my business the kindling it needs to attack larger markets. Niche Market software has a slew of features that are quite useful for achieving your marketing goals.
So, the next time you're interviewing for a small business, you can mention that Niche Market software was a great way your last manager had his/her marketing team compile data on the competition.
You can find a great piece of Niche Market Software @ http://www.marketsamurai.com/.
Monday, February 22, 2010
Virus and Spyware: A guide to performing your own maintenence part 2 of 2
In this part of my 2 part guide I'll be addressing the troubling topic of virus's providing you with some tips and techniques on how to manage the issues associated with them.
A great anti-virus program I've been using lately is Avast Antivirus. This is a great free antivirus program that utilizes minimal system resources and is very easy to setup. If your a technical person you may like these features:
*Definable heruistic levels for various scanning types.
*Rootkit scan upon startup.
*Custom scan profiles w/dozens of parameters
*Real-time scanning of web access, email, IM, P2P with independently definable scanning parameters.
So why not use a popular program like Norton and McAfee?
Ever notice that as soon as you install one of these products on your computer your PC begins to slow to a creeping crawl? Ever get locked out of your internet because of your firewall? Or how about when Norton just plain breaks preventing web browsing, access to your files, and use of your wireless. If these have never happened to you wonderful. If they have I'm not surprised. These are common problems with McAfee and Norton products as they often interact with areas of your Windows they simply should not.
Besides why pay for protection when you can get it for free!
Avast! isn't the only free anti-virus out there Ryan!
Your absolutely right. Don't just take my word for it find out for yourself. There are some great products out there. Antivir, AVG Free, just to name a couple. Avast is a great start for people looking to install protection that is very effective right out of the box so to speak.
You can find Avast! Anti-Virus Here: http://www.avast.com/free-antivirus-download
A great anti-virus program I've been using lately is Avast Antivirus. This is a great free antivirus program that utilizes minimal system resources and is very easy to setup. If your a technical person you may like these features:
*Definable heruistic levels for various scanning types.
*Rootkit scan upon startup.
*Custom scan profiles w/dozens of parameters
*Real-time scanning of web access, email, IM, P2P with independently definable scanning parameters.
So why not use a popular program like Norton and McAfee?
Ever notice that as soon as you install one of these products on your computer your PC begins to slow to a creeping crawl? Ever get locked out of your internet because of your firewall? Or how about when Norton just plain breaks preventing web browsing, access to your files, and use of your wireless. If these have never happened to you wonderful. If they have I'm not surprised. These are common problems with McAfee and Norton products as they often interact with areas of your Windows they simply should not.
Besides why pay for protection when you can get it for free!
Avast! isn't the only free anti-virus out there Ryan!
Your absolutely right. Don't just take my word for it find out for yourself. There are some great products out there. Antivir, AVG Free, just to name a couple. Avast is a great start for people looking to install protection that is very effective right out of the box so to speak.
You can find Avast! Anti-Virus Here: http://www.avast.com/free-antivirus-download
Monday, February 15, 2010
A quick and easy way to manage your IP addresses
If you find yourself constantly managing your IP addresses, Proxy addresses, and windows workgroup information, I have a great free tool for you. Free IP Switcher provides a nice set of features that come standard with most IP changers but takes it a step further and places it all in a clean interface. You can create IP profiles for multiple hardware interfaces, set machine name and workgroup profiles, and set Proxy Server Settings for secure browsing:

If you use your laptop at home and at the office, this will save you the trouble of having to switch back and forth between IP addresses and Filesharing workgroup names.
The interface is very clean and so far I found it to be bug free. Free IP Switcher can also be configured to start up automatically as windows boots.
You can find Free IP Switcher here:
http://www.eusing.com/ipswitch/free_ip_switcher.htm
Monday, February 1, 2010
Virus's and Spyware: A Guide to performing your own Maintenance Part 1 of 2
In this 2-part series I'll introduce some easy ways to keep your PC clean, and protect against viral and malware infection. I'm going to outline free software to help you accomplish this. Where to get it and how to set it up.
If you'd like more information on virus' and how they work, click on one of the links below:
What is Malware?
What is a virus?
What is spyware?
Before we begin I'd like to clarify that there is no substitute for a trained technician. If you are in danger of losing your data, I recommend you seek professional assistance.
If you own a PC you've probably encountered a virus. At this very moment there is undoubtedly spyware sitting somewhere in your computer. While you struggle protecting yourself from unwanted programs, Mac users will boast how proud they are that Mac's never get infected. All the while, you shell out hundreds of dollars a year taking your computer into a shop to clean out all the junk you've piled on to your system. Frustrating to say the least.
At the end of my 2 part guide you will be able to perform your own system maintenance and dramatically increase the health of your computer. I'll cover methods of freeing up your hard drive space, protecting your browser from spyware, and keeping your computer safe from infection.
I would estimate you can eliminate 60% of unwanted software by following these guidelines:
Curiosity kills both cats and your computer!
Now that we've covered some basic habits to prevent infection, lets take a look at building up a good set of tools to perform some regular maintenance. A weekly clean for you will consist of the following:
Doing a weekly scan with these programs will save you a heap of headache and money. Spybot and MalwareBytes will provide you a solid set of Malware and Spyware detection services. Cleanup! performs extensive system cleaning of your temporary file directories that eat up drive space over time. Avast anti-virus is an excellent, completely free, anti-virus program. Avast has added a few really nice features recently that sold me on their freeware version.
MalwareBytes Anti-Malware
Open your web-browser and go to www.malwarebytes.org and click the "download free version" link then install MalwareBytes on your system. Perform an update of MalwareBytes before scanning your system. Doing this will ensure Malwarebytes is scanning with the latest malware database :

To perform a full system scan:
-From the Scanner section, click on the "Perform full scan" toggle
-Click the scan button below:

If MalwareBytes finds any infected objects:
-Click the "Show Results" button in the bottom right of the window.
-From the results window, click "Delete All".
Some items aren't always deleted right away so you may be asked to restart your computer to complete the cleaning.
Spybot S&D
Go to www.safer-networking.org and download Spybot S&D. During the installation process you will be asked if you would like to perform a software update of spybot. Clicking "yes" will bring up the window shown below:

The list shown above is a list of updates. Be sure to update all the items titled "detection rules" and click "Download". After the download completes, Spybot should start normally.
Next, were going to enable a very important area of spybot called "Immunize". This will protect your browser from nearly 200,000 types of unwanted programs. To access this feature, click the "immunize" button in the left section of Spybot's main menu:

In the immunize page, take notice of the top right of the page:

The top right of this window will show you the anti-spyware it is aware of and actively protecting against (Protected), the files yet to be loaded (unprotected), and the Total files spybot has at its disposal:

To load all entries, click Immunize:

Once completed, your browser will be loaded will Spybot's immunization database.
Now your ready to perform your first scan. Spybot's web site has some very well written resources if you'd like a guided walkthrough of performing your first scan, visit Safer Networking for additional info on scans and how to interpret scan results with Spybot.
CleanUp!
CleanUp! is a great free program that will clean windows of temporary files. Temporary files are created in many different ways as you make changes to your computer and run software. Over a period of 1 month an average computer can accumulate roughly 500mb of temporary files or "Junk" files. After 6 months you could easily find yourself with a large portion of disk space vanishing into thin air. You can avoid losing out on precious hard drive space with this free program.
The interface may not look like much but it is very effective at cleaning your hard drive:

Click this link to Stevegould.org to download CleanUp!. Before downloading this program take a second to read this introduction then scroll to the bottom of the page and click "next". Next, click the link shown here:
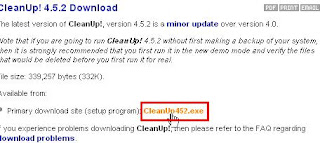
After you download and install CleanUp!, your first run of CleanUp! will throw up this message:

If you click yes, CleanUp! will scan, show you results, and won't delete anything. If you click no, a normal scan will be conducted and will delete all junk files it finds. Be sure to close all your browser windows before you start your scan otherwise you'll see this window:

love the flush! if you'd like to turn that off scroll to the bottom of this section. At the end of the scan your results will be shown in the main CleanUp! Window:

I recommend a quick scroll through the list of deleted items to see what CleanUp! deleted from your system. Its good to have a rough idea where these files may be nestled in the event you'd like to perform a manual removal of these junk files. If you ran CleanUp! in Demonstration Mode, close cleanup and open it back up again to run it in normal mode.
Disable the loud Flush. In the Cleanup main window click the options button. Then uncheck the check box shown here:

Avast Antivirus
Avast Antivirus will be covered in part 2 of this entry. Virus detection and removal offers a few extra challenges and I think I've addressed a nice chunk of info already. In my next post I'll explain some of the key features you'll want to look for in anti-virus software and how to use those features to your advantage.
Hope this helps! Happy cleaning!
A big thanks to uncle Rob for his years of guidance!
If you'd like more information on virus' and how they work, click on one of the links below:
What is Malware?
What is a virus?
What is spyware?
Before we begin I'd like to clarify that there is no substitute for a trained technician. If you are in danger of losing your data, I recommend you seek professional assistance.
If you own a PC you've probably encountered a virus. At this very moment there is undoubtedly spyware sitting somewhere in your computer. While you struggle protecting yourself from unwanted programs, Mac users will boast how proud they are that Mac's never get infected. All the while, you shell out hundreds of dollars a year taking your computer into a shop to clean out all the junk you've piled on to your system. Frustrating to say the least.
At the end of my 2 part guide you will be able to perform your own system maintenance and dramatically increase the health of your computer. I'll cover methods of freeing up your hard drive space, protecting your browser from spyware, and keeping your computer safe from infection.
I would estimate you can eliminate 60% of unwanted software by following these guidelines:
- Avoid being "click-happy" while web browsing. Closely examine what you are clicking and decide if it is explicitly where you want to go. Practice a healthy sense of caution.
- Use an ad-blocker. A number 1 source of Malware and Spyware are ads that claim they are legitimate products or services. If you receive a pop-up, study it carefully. It will usually contain a "close" or "cancel" button. If it is a window, DO NOT click anywhere in the ad simply close the window by clicking the "X" in the top right of the window.
- Don't respond to fake messages on Porn sites. Embarrassing but true. Majority of computers I've worked on have gotten infected because of reckless porn browsing. If you've taken your computer in because of reckless browsing, a trained technician can spot your browsing habits a mile away.
Curiosity kills both cats and your computer!
Now that we've covered some basic habits to prevent infection, lets take a look at building up a good set of tools to perform some regular maintenance. A weekly clean for you will consist of the following:
Doing a weekly scan with these programs will save you a heap of headache and money. Spybot and MalwareBytes will provide you a solid set of Malware and Spyware detection services. Cleanup! performs extensive system cleaning of your temporary file directories that eat up drive space over time. Avast anti-virus is an excellent, completely free, anti-virus program. Avast has added a few really nice features recently that sold me on their freeware version.
MalwareBytes Anti-Malware
Open your web-browser and go to www.malwarebytes.org and click the "download free version" link then install MalwareBytes on your system. Perform an update of MalwareBytes before scanning your system. Doing this will ensure Malwarebytes is scanning with the latest malware database :

To perform a full system scan:
-From the Scanner section, click on the "Perform full scan" toggle
-Click the scan button below:

If MalwareBytes finds any infected objects:
-Click the "Show Results" button in the bottom right of the window.
-From the results window, click "Delete All".
Some items aren't always deleted right away so you may be asked to restart your computer to complete the cleaning.
Spybot S&D
Go to www.safer-networking.org and download Spybot S&D. During the installation process you will be asked if you would like to perform a software update of spybot. Clicking "yes" will bring up the window shown below:

The list shown above is a list of updates. Be sure to update all the items titled "detection rules" and click "Download". After the download completes, Spybot should start normally.
Next, were going to enable a very important area of spybot called "Immunize". This will protect your browser from nearly 200,000 types of unwanted programs. To access this feature, click the "immunize" button in the left section of Spybot's main menu:

In the immunize page, take notice of the top right of the page:

The top right of this window will show you the anti-spyware it is aware of and actively protecting against (Protected), the files yet to be loaded (unprotected), and the Total files spybot has at its disposal:

To load all entries, click Immunize:

Once completed, your browser will be loaded will Spybot's immunization database.
Now your ready to perform your first scan. Spybot's web site has some very well written resources if you'd like a guided walkthrough of performing your first scan, visit Safer Networking for additional info on scans and how to interpret scan results with Spybot.
CleanUp!
CleanUp! is a great free program that will clean windows of temporary files. Temporary files are created in many different ways as you make changes to your computer and run software. Over a period of 1 month an average computer can accumulate roughly 500mb of temporary files or "Junk" files. After 6 months you could easily find yourself with a large portion of disk space vanishing into thin air. You can avoid losing out on precious hard drive space with this free program.
The interface may not look like much but it is very effective at cleaning your hard drive:

Click this link to Stevegould.org to download CleanUp!. Before downloading this program take a second to read this introduction then scroll to the bottom of the page and click "next". Next, click the link shown here:

After you download and install CleanUp!, your first run of CleanUp! will throw up this message:

If you click yes, CleanUp! will scan, show you results, and won't delete anything. If you click no, a normal scan will be conducted and will delete all junk files it finds. Be sure to close all your browser windows before you start your scan otherwise you'll see this window:

love the flush! if you'd like to turn that off scroll to the bottom of this section. At the end of the scan your results will be shown in the main CleanUp! Window:

I recommend a quick scroll through the list of deleted items to see what CleanUp! deleted from your system. Its good to have a rough idea where these files may be nestled in the event you'd like to perform a manual removal of these junk files. If you ran CleanUp! in Demonstration Mode, close cleanup and open it back up again to run it in normal mode.
Disable the loud Flush. In the Cleanup main window click the options button. Then uncheck the check box shown here:

Avast Antivirus
Avast Antivirus will be covered in part 2 of this entry. Virus detection and removal offers a few extra challenges and I think I've addressed a nice chunk of info already. In my next post I'll explain some of the key features you'll want to look for in anti-virus software and how to use those features to your advantage.
Hope this helps! Happy cleaning!
A big thanks to uncle Rob for his years of guidance!
Labels:
avast,
freeware,
malware removal,
spybot,
spyware,
virus removal
Sunday, January 31, 2010
Bittorent Series Part 4 of 4: Make your own torrent
Creating your own torrent file and uploading it is a snap. In this final part of my torrent series I'll be walking you through the setup process of a publicly available torrent file anyone can download.
A great thing I've always loved about P2P file sharing is the active and necessary role people play to create an infrastructure of freely available content. No knowledge of how P2P works is necessary to benefit from its availability. By uploading your own torrents you take an active role in the free distribution of information. Torrents are not always comprised of pirated software and illegal movies. They can be custom compilations of your favorite freeware programs, a film you recently produced you'd like to distribute, or old books you recently converted to pdf's. Whatever it may be you can torrent just about anything. If your looking to upload an extremely popular torrent, a "public torrent" is ideal for you.
Step 1: Account Setup
First, you will need to create an account with a torrent search engine. In this tutorial were going to use Utorrent as our torrent client of choice, and btjunkie.org as our torrent search engine.
To do this, go to btjunkie.org and click the member link:

Next, click the sign up link:

You will be taken to the account creation page:

You will need a vaild email address for this. You will be sent an email verification. In that email, you will need to click the "verify account" link. Now your ready to begin uploading torrents.
Step 2: Creating your first torrent file
Before we move on, I'd like to take a second to explain how this next part works. If you already understand how torrent metadata works then skip this explanation. I'm going to refer back to my analogy I used in Part 2 where I associated computers and internet connections as businesses connected by roads and freeways. Think of a torrent file as an informational roadsign along one of these roadways. This sign will guide people to your store. When you create a "torrent" file, what your doing is setting up a roadsign that tells others several important pieces of information:
1) Where the computer or server containing the file is located.
2) Where the file is located on said computer or server.
3) What torrent tracking servers will be paying attention to this file.
4) Is this torrent private or is it public.
So again, a torrent is not the actual file you are sharing. It is a file containing the information a torrent client will need to locate desired data as it exists on one or multiple computers. In this case, since you are creating a torrent to share a file on your computer, you will be the sole owner of that file until another person completes a download of your file. They will then become a "seeder" of that file and begin uploading in the same way you are.
So lets begin shall we...
Open Utorrent, click the "File" menu, then click "Create New Torrent" from the drop down menu. You can also do this by using the hotkey "Ctrl + N" :

Don't be intimidated by the next window:

This is where we actually create our roadsign. Since we are creating a basic public torrent file we only need to follow 4 steps:
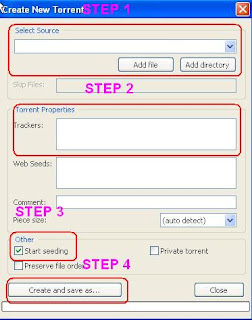
Step 1
Locate the file or folder you want to share with others by clicking the "add file" or "add directory" button. This can be a compressed archive like a zip file or rar file, program executable, movie, anything. I have a collection of great PC technician tools I'd like to share with others that I've compressed into a single rar file.
Step 2
This part can be a little tricky for some. We're going to add a tracker server address for your torrent. . A torrent server address looks like any other website address (http://blah.com:80) with a port number appended to it. I've included a short list of working torrent tracker addresses you can use to get you started. Simply copy and paste one or more of the addresses found below into the the step 2 box shown above. Be sure there is a space separating each address or utorrent will not recognize the address:
http://denis.stalker.h3q.com:6969/announce
http://tpb.tracker.prq.to/announce
http://tracker.prq.to/announce
http://tracker.torrent.to:2710/announce
http://tv.tracker.prq.to/announce
*SPEED BOOST TIP: If your downloading a torrent with a low amount of seeders you can add more by adding additional tracker addresses to the torrent file to give you a possible boost in speed. Simply right click on your download and go to properties. There you will find the tracker server list which you can modify by adding any number of tracker address.
Step 3
Ensure that the "Start Seeding" check box is filled. This will start seeding your torrent the moment it's created.
Step 4
Now your done. You can click "Create torrent" and save it as a descriptive file name that will help tell people what your torrent is. Since this is not the title people will see when they search for your torrent there's no need to include a large file name.
Step 3: Make your torrent available to others
Just a quick note. If you'd like to share your torrent with a small group of friends rather than make it available to anyone able to search btjunkie, you can email the torrent you just created to a friend. Once they receive the torrent they can begin downloading your file immediately. For those familiar with FTP services this feature could serve as an alternative in some situations.
Let's go back to btjunkie.org and login to your account by going to the members section then enter your username and password. Once logged in, the upload feature will be available to you:


Click upload and you will be taken to the upload page:

Step 1
Click browse and navigate to the torrent you just created.
Step 2
Create a label for your torrent that search engines will use to identify your torrent. It helps to make your description long containing keywords that may help your torrent show up in more searches. For example, I called my file "Great PC utilities Memtest 0&O defrag Anti-Malware". If someone searches for any of these terms my file will show up in their search.
Step 3
Select the Category you'd like your torrent to fall under. This helps users find your torrent easier when they refine a search to include a specific category.
Your almost done. Enter a Capcha then scroll dow and click the verification bubble, then hit upload. After the upload completes you should see something like this:

And thats it. After a few hours or so your search will eventually start showing up in btjunkie.org.
Conclusion
If you have read all 4 parts of my Bittorrent series, you should have a much better understanding for how torrents work and how to utilize them as a valuable resource. I recommend doing your own research on torrents since the topics I wasn't able to cover in this tutorial are NUMEROUS!
Torrents are merely the latest evolution in P2P file sharing. It's hard to say what direction the free distribution of information will take in the coming decade but its very exciting to know it can only get better from here. The file sharing provides some valuable tools for learning which no individual should be restricted from or hindered by.
A great thing I've always loved about P2P file sharing is the active and necessary role people play to create an infrastructure of freely available content. No knowledge of how P2P works is necessary to benefit from its availability. By uploading your own torrents you take an active role in the free distribution of information. Torrents are not always comprised of pirated software and illegal movies. They can be custom compilations of your favorite freeware programs, a film you recently produced you'd like to distribute, or old books you recently converted to pdf's. Whatever it may be you can torrent just about anything. If your looking to upload an extremely popular torrent, a "public torrent" is ideal for you.
Step 1: Account Setup
First, you will need to create an account with a torrent search engine. In this tutorial were going to use Utorrent as our torrent client of choice, and btjunkie.org as our torrent search engine.
To do this, go to btjunkie.org and click the member link:

Next, click the sign up link:

You will be taken to the account creation page:

You will need a vaild email address for this. You will be sent an email verification. In that email, you will need to click the "verify account" link. Now your ready to begin uploading torrents.
Step 2: Creating your first torrent file
Before we move on, I'd like to take a second to explain how this next part works. If you already understand how torrent metadata works then skip this explanation. I'm going to refer back to my analogy I used in Part 2 where I associated computers and internet connections as businesses connected by roads and freeways. Think of a torrent file as an informational roadsign along one of these roadways. This sign will guide people to your store. When you create a "torrent" file, what your doing is setting up a roadsign that tells others several important pieces of information:
1) Where the computer or server containing the file is located.
2) Where the file is located on said computer or server.
3) What torrent tracking servers will be paying attention to this file.
4) Is this torrent private or is it public.
So again, a torrent is not the actual file you are sharing. It is a file containing the information a torrent client will need to locate desired data as it exists on one or multiple computers. In this case, since you are creating a torrent to share a file on your computer, you will be the sole owner of that file until another person completes a download of your file. They will then become a "seeder" of that file and begin uploading in the same way you are.
So lets begin shall we...
Open Utorrent, click the "File" menu, then click "Create New Torrent" from the drop down menu. You can also do this by using the hotkey "Ctrl + N" :

Don't be intimidated by the next window:

This is where we actually create our roadsign. Since we are creating a basic public torrent file we only need to follow 4 steps:

Step 1
Locate the file or folder you want to share with others by clicking the "add file" or "add directory" button. This can be a compressed archive like a zip file or rar file, program executable, movie, anything. I have a collection of great PC technician tools I'd like to share with others that I've compressed into a single rar file.
Step 2
This part can be a little tricky for some. We're going to add a tracker server address for your torrent. . A torrent server address looks like any other website address (http://blah.com:80) with a port number appended to it. I've included a short list of working torrent tracker addresses you can use to get you started. Simply copy and paste one or more of the addresses found below into the the step 2 box shown above. Be sure there is a space separating each address or utorrent will not recognize the address:
http://denis.stalker.h3q.com:6969/announce
http://tpb.tracker.prq.to/announce
http://tracker.prq.to/announce
http://tracker.torrent.to:2710/announce
http://tv.tracker.prq.to/announce
*SPEED BOOST TIP: If your downloading a torrent with a low amount of seeders you can add more by adding additional tracker addresses to the torrent file to give you a possible boost in speed. Simply right click on your download and go to properties. There you will find the tracker server list which you can modify by adding any number of tracker address.
Step 3
Ensure that the "Start Seeding" check box is filled. This will start seeding your torrent the moment it's created.
Step 4
Now your done. You can click "Create torrent" and save it as a descriptive file name that will help tell people what your torrent is. Since this is not the title people will see when they search for your torrent there's no need to include a large file name.
Step 3: Make your torrent available to others
Just a quick note. If you'd like to share your torrent with a small group of friends rather than make it available to anyone able to search btjunkie, you can email the torrent you just created to a friend. Once they receive the torrent they can begin downloading your file immediately. For those familiar with FTP services this feature could serve as an alternative in some situations.
Let's go back to btjunkie.org and login to your account by going to the members section then enter your username and password. Once logged in, the upload feature will be available to you:


Click upload and you will be taken to the upload page:

Step 1
Click browse and navigate to the torrent you just created.
Step 2
Create a label for your torrent that search engines will use to identify your torrent. It helps to make your description long containing keywords that may help your torrent show up in more searches. For example, I called my file "Great PC utilities Memtest 0&O defrag Anti-Malware". If someone searches for any of these terms my file will show up in their search.
Step 3
Select the Category you'd like your torrent to fall under. This helps users find your torrent easier when they refine a search to include a specific category.
Your almost done. Enter a Capcha then scroll dow and click the verification bubble, then hit upload. After the upload completes you should see something like this:

And thats it. After a few hours or so your search will eventually start showing up in btjunkie.org.
Conclusion
If you have read all 4 parts of my Bittorrent series, you should have a much better understanding for how torrents work and how to utilize them as a valuable resource. I recommend doing your own research on torrents since the topics I wasn't able to cover in this tutorial are NUMEROUS!
Torrents are merely the latest evolution in P2P file sharing. It's hard to say what direction the free distribution of information will take in the coming decade but its very exciting to know it can only get better from here. The file sharing provides some valuable tools for learning which no individual should be restricted from or hindered by.
Saturday, January 30, 2010
Part 3 of 4: Hunting torrents
These days its fairly simple to find torrent files on the web. The growing availability of torrent search engines make it easy for anyone to find the latest movie releases and high priced computer software. Finding the correct torrent to download can sometimes be a mine field of follies. A search for a very popular torrent might yield dozens of results with the same heading. Among them usually 2 or 3 of these files you can be fairly certain will be free of virus's, work without a hitch, and finish quickly. In part 3 of my torrent series I'm going to cover some of the basics on finding and choosing torrents. I'll also introduce the topic of Private Torrent Trackers and why they are private and what you can gain by using them.
Step 1: File Size
For those new to torrents you really only need to be aware of 3 things. The relationship between seeders and leechers, a basic knowledge of file sizes, and process of elimination. Seeders and leechers serve as the foundation for why torrents work so well and why they are so controversial. If you need to know more about seeders and leechers click here.
For this how-to, I'm going to do a torrent search on btjunkie.org for Windows 7:

This is a nice result on my search. An easy way to eliminate what is NOT the torrent I'm looking for is to take a look at the file size. Since I know windows 7 is a large Operating System distributed on a DVD, I can instantly rule out files smaller than 2GB. The same process can be applied to Movies as well. But we will address that later.
Step 2: Seeders and Leechers...
I've read quite a few articles on what the ideal amount of seeders and leechers should be. Although some say it's debatable, you ideally want more seeders than leechers. If that is not an option, the closest you can get to a 1 to 1 ratio is usually best since this will give you a large pool of sources to download from without too much strain on each source. So lets apply this to our results. You can see the first result on the list has more seeds (sources) but significantly more people downloading it (leechers) the ratio here is about 1 to 1.3. The next one down is slightly more in our favor since there are more seeders than leechers here. Both offer good speeds and since a large amount of people are circulating this file, it must mean that this is a fully working copy of windows right?
Step 3: The all important comments section
When I click on the first file in my list, I get taken to the torrent details section:

At the top we see the torrent trackers hosting this file, the size of the file, the date added and so on. As I scroll down a bit I start to enter the all important comments section. This is where you can save yourself a lot of wasted time. By reading through the comments on this torrent

They didn't say some very good things about this file. By taking 15 seconds to read this section, I just saved myself an entire evening of disapointment not to mention a wasted DVD-R. READ THE COMMENTS OF YOUR TORRENTS. This is all important and very easy to do. Some torrents can also be password protected and a quick visit to this section may reveal the information you need to unlock your torrent.
Side Note
Now how does this apply to movies you ask. There are several types of movies you'll encounter in the torrent-verse. Workprints, screeners, dvd-rips, SVCD/VCD, and dvd-copy. Depending on how much time has gone by since the movie release, your movie will be in one or more of these formats. Before a movie goers have a chance to sit in a theater with a video camera, private showings for producers, film critics and big executives take place. Production companies will use what is known as A "workprint" or a digital cut of the movie to distribute for this purpose. You've probably seen this happen with movies like Wolverine: Origins where you were able to watch the movie start to finish even though it was clearly still in post production. Any time your watching a good quality movie before its been released in theaters your watching a workprint.
Workprints are torrents really worth hunting for. Workprints are not as common as Screeners but its worth the work if you find one since there is a clear difference in quality. The remaining formats I previously mentioned are good to familiarize yourself with. If your interested in more information on DVD-rips and VCD's I've provided some good resources below:
SmartRipper, a great freeware VOB file copier
A staple piece of software for DVD-rippers
Great guides for DVD-ripping
Not Freeware, Fully featured complete movie conversion suite that takes out all the guess work. I rarely recommend software you have to pay for but this tool really pays for itself in the amount of time you save.
Private Torrent Trackers: How they help, How they hurt
In the ol' days of file sharing, people would scour IRC, Bulletin Board Systems, and newsgroups to get their hands on the latest and greatest in pirated software even before there was such a thing as pirated software. On their dial-up connections, they spent thousands of hours downloading what would take us minutes to download now. Although the learning curve of finding these files has greatly diminished, avid and impatient file downloaders of the present take painstaking measures to be the first to find the latest leaked version of pirated software. They then make it their personal mission to distribute these files to the masses.
This may sound a bit shady, but believe it or not, there is a slew of Private torrent sites that allow you to browse through a collection of user posted torrents you may not find on larger torrent sites like thepiratebay.com and mininova. These Private trackers maintain a database of registered users and will require you to register an account with them before you can access their resources. There is also an even more elusive side to torrents that still uses the IRC format to communicate and send private torrent invites from their hosted trackers. This is an aspect of torrents I do not recommend beginners get involved in.
Pivate trackers exist is to allow the groups responsible for leaking or cracking files several layers of anonymity. By dispersing these files to a handful of cautious and experienced individuals, the direct link between the file and the distributor is broken. The file can then continue to be distributed by just about anyone that participates torrent file sharing. At this point, thousands of people are sharing the file and no one really knows where it really came from. Groups will often tag the file with their group name but their real identity and physical location remains unknown. This process is not a product of over zealous hackers indulging their ego, this is actually a necessary part of torrent sharing.
So if its necessary, how does it hurt the torrent process?
By segmenting torrents into private servers, similar torrent files exist on multiple servers. For instance, you may have 2 or more Windows 7 torrents that are essentially the same torrent in every way but tracked separately on private servers. By porting this collection of torrents over to a single torrent file with a complete list of trackers, you can eliminate superfluous files. This would basically allow a tracker to pool seeders and leechers that would otherwise exist separately on private servers to a single torrent. Torrent files with 0 seeders 0 leechers would diminish and your files would download faster. Basically, private servers, although necessary, are unfortunately inefficient and clutter the internet with extra stuff we don't need. But clutter is nothing new for the web now is it.
Step 1: File Size
For those new to torrents you really only need to be aware of 3 things. The relationship between seeders and leechers, a basic knowledge of file sizes, and process of elimination. Seeders and leechers serve as the foundation for why torrents work so well and why they are so controversial. If you need to know more about seeders and leechers click here.
For this how-to, I'm going to do a torrent search on btjunkie.org for Windows 7:

This is a nice result on my search. An easy way to eliminate what is NOT the torrent I'm looking for is to take a look at the file size. Since I know windows 7 is a large Operating System distributed on a DVD, I can instantly rule out files smaller than 2GB. The same process can be applied to Movies as well. But we will address that later.
Step 2: Seeders and Leechers...
I've read quite a few articles on what the ideal amount of seeders and leechers should be. Although some say it's debatable, you ideally want more seeders than leechers. If that is not an option, the closest you can get to a 1 to 1 ratio is usually best since this will give you a large pool of sources to download from without too much strain on each source. So lets apply this to our results. You can see the first result on the list has more seeds (sources) but significantly more people downloading it (leechers) the ratio here is about 1 to 1.3. The next one down is slightly more in our favor since there are more seeders than leechers here. Both offer good speeds and since a large amount of people are circulating this file, it must mean that this is a fully working copy of windows right?
Step 3: The all important comments section
When I click on the first file in my list, I get taken to the torrent details section:

At the top we see the torrent trackers hosting this file, the size of the file, the date added and so on. As I scroll down a bit I start to enter the all important comments section. This is where you can save yourself a lot of wasted time. By reading through the comments on this torrent

They didn't say some very good things about this file. By taking 15 seconds to read this section, I just saved myself an entire evening of disapointment not to mention a wasted DVD-R. READ THE COMMENTS OF YOUR TORRENTS. This is all important and very easy to do. Some torrents can also be password protected and a quick visit to this section may reveal the information you need to unlock your torrent.
Side Note
Now how does this apply to movies you ask. There are several types of movies you'll encounter in the torrent-verse. Workprints, screeners, dvd-rips, SVCD/VCD, and dvd-copy. Depending on how much time has gone by since the movie release, your movie will be in one or more of these formats. Before a movie goers have a chance to sit in a theater with a video camera, private showings for producers, film critics and big executives take place. Production companies will use what is known as A "workprint" or a digital cut of the movie to distribute for this purpose. You've probably seen this happen with movies like Wolverine: Origins where you were able to watch the movie start to finish even though it was clearly still in post production. Any time your watching a good quality movie before its been released in theaters your watching a workprint.
Workprints are torrents really worth hunting for. Workprints are not as common as Screeners but its worth the work if you find one since there is a clear difference in quality. The remaining formats I previously mentioned are good to familiarize yourself with. If your interested in more information on DVD-rips and VCD's I've provided some good resources below:
SmartRipper, a great freeware VOB file copier
A staple piece of software for DVD-rippers
Great guides for DVD-ripping
Not Freeware, Fully featured complete movie conversion suite that takes out all the guess work. I rarely recommend software you have to pay for but this tool really pays for itself in the amount of time you save.
Private Torrent Trackers: How they help, How they hurt
In the ol' days of file sharing, people would scour IRC, Bulletin Board Systems, and newsgroups to get their hands on the latest and greatest in pirated software even before there was such a thing as pirated software. On their dial-up connections, they spent thousands of hours downloading what would take us minutes to download now. Although the learning curve of finding these files has greatly diminished, avid and impatient file downloaders of the present take painstaking measures to be the first to find the latest leaked version of pirated software. They then make it their personal mission to distribute these files to the masses.
This may sound a bit shady, but believe it or not, there is a slew of Private torrent sites that allow you to browse through a collection of user posted torrents you may not find on larger torrent sites like thepiratebay.com and mininova. These Private trackers maintain a database of registered users and will require you to register an account with them before you can access their resources. There is also an even more elusive side to torrents that still uses the IRC format to communicate and send private torrent invites from their hosted trackers. This is an aspect of torrents I do not recommend beginners get involved in.
Pivate trackers exist is to allow the groups responsible for leaking or cracking files several layers of anonymity. By dispersing these files to a handful of cautious and experienced individuals, the direct link between the file and the distributor is broken. The file can then continue to be distributed by just about anyone that participates torrent file sharing. At this point, thousands of people are sharing the file and no one really knows where it really came from. Groups will often tag the file with their group name but their real identity and physical location remains unknown. This process is not a product of over zealous hackers indulging their ego, this is actually a necessary part of torrent sharing.
So if its necessary, how does it hurt the torrent process?
By segmenting torrents into private servers, similar torrent files exist on multiple servers. For instance, you may have 2 or more Windows 7 torrents that are essentially the same torrent in every way but tracked separately on private servers. By porting this collection of torrents over to a single torrent file with a complete list of trackers, you can eliminate superfluous files. This would basically allow a tracker to pool seeders and leechers that would otherwise exist separately on private servers to a single torrent. Torrent files with 0 seeders 0 leechers would diminish and your files would download faster. Basically, private servers, although necessary, are unfortunately inefficient and clutter the internet with extra stuff we don't need. But clutter is nothing new for the web now is it.
Friday, January 29, 2010
Part 2 of 4: Configuring Utorrent
In this post I'll be covering concepts of torrents and provide you with some useful tips on how to configure utorrent to help keep you under the radar while maximizing bandwidth.
When you first install utorrent you'll be asked to do a quick speed test and define the "port" you'd like utorrent to utilize. The window I'm talking about looks like this:

This area of Utorrent allows you to do two things. One, define and test your "port" which others with use to connect to you. And two, perform a speed test giving you valuable information you will need later in this tutorial.
Now some of you may be asking "what the heck is a port?". Well to put it the simply, think of your internet connection like a freeway, ports like a big valet parking lot, and your computer as a store where other computers pull up to your store. When you browse a web page or start a download, a car pulls up to your store. The valet attendant takes the drivers keys, makes a note of the car, and what stall it will be parked at. Then the driver and his passengers enter your store. When this lot fills up, your store becomes very cramped making it difficult for people to move around in. By telling Utorrent to use a certain number of ports, it makes the valet attendant's job much easier and keeps your store from getting to cramped for your customers. Simple right!
Step one: Determine Your Speed
Upon installing Utorrent you will be shown the window I previously mentioned. Otherwise you can access this window by opening Utorrent, and clicking Options >> Speed Guide.
Why is knowing your bandwidth so important you ask?
As a torrent user you face the balancing act of maintaining excellent speed without the over consumption of resources. If your a casual downloader of a few torrents a week, this part will not be so crucial for you. But if your consuming over 10gb of space a week you may want to take some time doing the math.
1) Take a second to open the Speed Guide in Utorrent and click on the "Run Speed Test at dslreports.com" button.
2) Once the web site opens, click the first test called "flash 8 plugin speed test".
3) Next your going to be shown a list of servers. Since we want to find out our maximum potential bandwidth we want to pick a location closest to us. Because, I am doing this test in Oakland, I'm going to select the Server in San Francisco to perform my bandwidth test:

When your test finishes, it will display your approximate download and upload speed. You'll want to write this down for later use. With this information we can move on to step 2.
Step 2: Configure port usage and bandwidth
In this step were going to tell Utorrent exactly how much of our available bandwidth we'd like to use and how many "parking spots" or ports it will use at any given time. I'd like you to pop into utorrrent's preferences menu:

Select Bandwidth from the left side of the window:

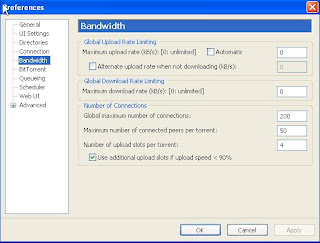
Questions you may be asking yourself at this point is "Won't reducing my download speed slow my torrents? What do I have to gain from reducing the speed?" Very valid questions.
The answer is simple: The combined speed at which all of your torrents are downloading will never reach the overall maximum bandwidth of your internet connection. Limiting Utorrent's bandwidth usage is important if you have 2 or more computers on your network. Moreover, if your using anything less than a cable internet connection, other applications that use an internet connection will become completely unresponsive. If your the only person on your network using a high speed internet connection and don't have a problem with dedicating all of your bandwidth to torrent downloads its your call.
So how do we determine what our optimal bandwidth usage should be?
Well, since our speed test result was in Kilobits and the setting we want to change in Utorrent is measured in Kilobytes, we need to convert kilobits to kilobytes. For more info on the relationship between kilobits and kilobytes pay a quick visit to this article @ speedguide :
A little bit of math is required for this
your download result from the speedtest / 8 = kbytes /sec
ex. My speedtest download result was 8017 Kbits /sec. I can round this off to 8000 Kbits /sec to simplify things, then divide it by 8 to get 1000 kbytes /sec.
My maximum bandwidth is roughly 1000 kbps.
A good download speed for Utorrent is about 75% to 85% of your maximum bandwidth. So, since 80% of 1000kbps is 800kbps I am going to use 800 for the setting here:

Ill rarely hit this limit but it can become important to set one when your downloading 5 or more torrents at once. *See bottom of this post for an advance tip on really opening up your bandwidth.
We can use the same process to determine our maximum Upload rate also. Using the "upload" results from your speed test, we can determine the ideal maximum upload speed the same way we determined our maximum download speed. After you have completed the conversion, plug in the number in the "Maximum Upload Rate" box.
Next, were going to tell Utorrent exactly how many ports to use for uploads and downloads.
A big problem I notice with torrent downloading is excessive port usage. This is where the relationship between ports and bandwidth becomes very clear. If you live in a house with many people on the internet at once, your roommates are probably getting down on you all the time about your downloading habits. The the internet slows to a crawl when your pulling torrents and they can't even access their email. You've tried time and time again to reduce your maximum bandwidth but still have trouble with this. Reducing your port usage in Utorrent can solve this problem once and for all. With the right amount of reduction you will never see the slightest bit of slow down for your torrent downloads and still allow for others on your network to browse the web uninterrupted.
Why does this happen you ask?
Well lets refer back to our parking lot / store analogy. Think of the internet as a collection of stores, and the roads linking those stores as internet connections. Regardless of how big of a freeway you have connecting your store with others, your valetparking lot can only take so many cars. When your parking lot fills up with cars, the parking attendant is going to get very confused and frustrated. Your router in this analogy is a combination of the vallet attendant and the parking lot and becomes a bottleneck when managing torrents. By limiting the amount of parking stalls Utorrent uses, you leave space for other stores (computers on your network) to use the same parking lot. Also relieving a great deal of stress on your parking attendant.
Now that you have a fair idea of how ports work lets play with this setting in Utorrent. To find the best amount of ports to use for your torrent downloads and uploads you'll have to rely on simple trial and error. A good starting point for port reduction is to set the "Global Maximum Number of Connections" setting to 70:

So now that we have gone over some really important topics and laid some good ground work to make utorrent more efficient, lets take a look at how we can make utorrent more secure.
ISP's, government organizations, and digital media corporations have been trying to find ways to regulate Peer-to-Peer filesharing for a long time now. Yet each time they find ways to profit from file sharing or prosecute participants of file sharing, programmers and hackers find new ways to keep information freely available to anyone willing to learn how to get it. Currently, torrents are being tracked and regulated in two ways:
Step 2: Setting up your Security
Preventing your ISP from limiting your torrent traffic is as simple as clicking a check box in Utorrent. Open your Preferences menu and select Bittorrents from the list. Next, click the drop-down menu under Outgoing Protocol Encryption and select enabled:

Click apply then restart utorrent. Your outgoing traffic will be more difficult to detect by your ISP. .
Next, were going to setup what is known as an IPfilter. This step is optional since it also does not have any effect on your torrent speed and is a bit harder to do than previous topics. For a complete how to on setting up IPFiltering for Utorrent click here.
Basically, the IPfilter is a list of known server IP address's that pose as fake seeders and lechers. Utorrent will flag these IP address's as harmful and will refuse their connection attempts. The list is very extensive and contains tens of thousands of IPs. The list can also be updated. For those wondering if its worth the time spent to set this up, it really depends on the amount of torrents you download. I feel anyone willing to spend the time doing this will benefit from using an IPfilter but this step will have no affect on performance.
Last but not least if your running firewall software we need to make sure Utorrent is able to make connections unrestricted. Adding an exception will definitely have an affect on your torrent speed and will allow more seeders to give you the data you need to complete your download.
Allowing unrestricted interaction between utorrent and your internet connection will require a "firewall exception". By default, utorrent has a setting under Preferences >> Connection >> Add exception to windows firewall enabled by default. If you have windows firewall enabled, Utorrent will place an exception in windows firewall the moment its installed. Its best to refer to your firewall documentation to find out how to add an exception.
Many of the topics I have covered today can also be found at the utorrent connection setup page.
Advanced topic: Change the maximum TCP/IP Connections per port. Refer to this great how-to on opening up the maximum number of TCP/IP connections in windows.
When you first install utorrent you'll be asked to do a quick speed test and define the "port" you'd like utorrent to utilize. The window I'm talking about looks like this:

This area of Utorrent allows you to do two things. One, define and test your "port" which others with use to connect to you. And two, perform a speed test giving you valuable information you will need later in this tutorial.
Now some of you may be asking "what the heck is a port?". Well to put it the simply, think of your internet connection like a freeway, ports like a big valet parking lot, and your computer as a store where other computers pull up to your store. When you browse a web page or start a download, a car pulls up to your store. The valet attendant takes the drivers keys, makes a note of the car, and what stall it will be parked at. Then the driver and his passengers enter your store. When this lot fills up, your store becomes very cramped making it difficult for people to move around in. By telling Utorrent to use a certain number of ports, it makes the valet attendant's job much easier and keeps your store from getting to cramped for your customers. Simple right!
Step one: Determine Your Speed
Upon installing Utorrent you will be shown the window I previously mentioned. Otherwise you can access this window by opening Utorrent, and clicking Options >> Speed Guide.
Why is knowing your bandwidth so important you ask?
As a torrent user you face the balancing act of maintaining excellent speed without the over consumption of resources. If your a casual downloader of a few torrents a week, this part will not be so crucial for you. But if your consuming over 10gb of space a week you may want to take some time doing the math.
1) Take a second to open the Speed Guide in Utorrent and click on the "Run Speed Test at dslreports.com" button.
2) Once the web site opens, click the first test called "flash 8 plugin speed test".
3) Next your going to be shown a list of servers. Since we want to find out our maximum potential bandwidth we want to pick a location closest to us. Because, I am doing this test in Oakland, I'm going to select the Server in San Francisco to perform my bandwidth test:

When your test finishes, it will display your approximate download and upload speed. You'll want to write this down for later use. With this information we can move on to step 2.
Step 2: Configure port usage and bandwidth
In this step were going to tell Utorrent exactly how much of our available bandwidth we'd like to use and how many "parking spots" or ports it will use at any given time. I'd like you to pop into utorrrent's preferences menu:

Select Bandwidth from the left side of the window:


Questions you may be asking yourself at this point is "Won't reducing my download speed slow my torrents? What do I have to gain from reducing the speed?" Very valid questions.
The answer is simple: The combined speed at which all of your torrents are downloading will never reach the overall maximum bandwidth of your internet connection. Limiting Utorrent's bandwidth usage is important if you have 2 or more computers on your network. Moreover, if your using anything less than a cable internet connection, other applications that use an internet connection will become completely unresponsive. If your the only person on your network using a high speed internet connection and don't have a problem with dedicating all of your bandwidth to torrent downloads its your call.
So how do we determine what our optimal bandwidth usage should be?
Well, since our speed test result was in Kilobits and the setting we want to change in Utorrent is measured in Kilobytes, we need to convert kilobits to kilobytes. For more info on the relationship between kilobits and kilobytes pay a quick visit to this article @ speedguide :
A little bit of math is required for this
your download result from the speedtest / 8 = kbytes /sec
ex. My speedtest download result was 8017 Kbits /sec. I can round this off to 8000 Kbits /sec to simplify things, then divide it by 8 to get 1000 kbytes /sec.
My maximum bandwidth is roughly 1000 kbps.
A good download speed for Utorrent is about 75% to 85% of your maximum bandwidth. So, since 80% of 1000kbps is 800kbps I am going to use 800 for the setting here:

Ill rarely hit this limit but it can become important to set one when your downloading 5 or more torrents at once. *See bottom of this post for an advance tip on really opening up your bandwidth.
We can use the same process to determine our maximum Upload rate also. Using the "upload" results from your speed test, we can determine the ideal maximum upload speed the same way we determined our maximum download speed. After you have completed the conversion, plug in the number in the "Maximum Upload Rate" box.
Next, were going to tell Utorrent exactly how many ports to use for uploads and downloads.
A big problem I notice with torrent downloading is excessive port usage. This is where the relationship between ports and bandwidth becomes very clear. If you live in a house with many people on the internet at once, your roommates are probably getting down on you all the time about your downloading habits. The the internet slows to a crawl when your pulling torrents and they can't even access their email. You've tried time and time again to reduce your maximum bandwidth but still have trouble with this. Reducing your port usage in Utorrent can solve this problem once and for all. With the right amount of reduction you will never see the slightest bit of slow down for your torrent downloads and still allow for others on your network to browse the web uninterrupted.
Why does this happen you ask?
Well lets refer back to our parking lot / store analogy. Think of the internet as a collection of stores, and the roads linking those stores as internet connections. Regardless of how big of a freeway you have connecting your store with others, your valetparking lot can only take so many cars. When your parking lot fills up with cars, the parking attendant is going to get very confused and frustrated. Your router in this analogy is a combination of the vallet attendant and the parking lot and becomes a bottleneck when managing torrents. By limiting the amount of parking stalls Utorrent uses, you leave space for other stores (computers on your network) to use the same parking lot. Also relieving a great deal of stress on your parking attendant.
Now that you have a fair idea of how ports work lets play with this setting in Utorrent. To find the best amount of ports to use for your torrent downloads and uploads you'll have to rely on simple trial and error. A good starting point for port reduction is to set the "Global Maximum Number of Connections" setting to 70:

So now that we have gone over some really important topics and laid some good ground work to make utorrent more efficient, lets take a look at how we can make utorrent more secure.
ISP's, government organizations, and digital media corporations have been trying to find ways to regulate Peer-to-Peer filesharing for a long time now. Yet each time they find ways to profit from file sharing or prosecute participants of file sharing, programmers and hackers find new ways to keep information freely available to anyone willing to learn how to get it. Currently, torrents are being tracked and regulated in two ways:
- ISP's monitoring torrent traffic and limit the amount of traffic of this type.
- Organizations will create fake torrent seeders and lechers to dupe your torrent client into connecting to one of these servers. Once connected, a record of your IP address and your downloading is created.
Step 2: Setting up your Security
Preventing your ISP from limiting your torrent traffic is as simple as clicking a check box in Utorrent. Open your Preferences menu and select Bittorrents from the list. Next, click the drop-down menu under Outgoing Protocol Encryption and select enabled:

Click apply then restart utorrent. Your outgoing traffic will be more difficult to detect by your ISP. .
Next, were going to setup what is known as an IPfilter. This step is optional since it also does not have any effect on your torrent speed and is a bit harder to do than previous topics. For a complete how to on setting up IPFiltering for Utorrent click here.
Basically, the IPfilter is a list of known server IP address's that pose as fake seeders and lechers. Utorrent will flag these IP address's as harmful and will refuse their connection attempts. The list is very extensive and contains tens of thousands of IPs. The list can also be updated. For those wondering if its worth the time spent to set this up, it really depends on the amount of torrents you download. I feel anyone willing to spend the time doing this will benefit from using an IPfilter but this step will have no affect on performance.
Last but not least if your running firewall software we need to make sure Utorrent is able to make connections unrestricted. Adding an exception will definitely have an affect on your torrent speed and will allow more seeders to give you the data you need to complete your download.
Allowing unrestricted interaction between utorrent and your internet connection will require a "firewall exception". By default, utorrent has a setting under Preferences >> Connection >> Add exception to windows firewall enabled by default. If you have windows firewall enabled, Utorrent will place an exception in windows firewall the moment its installed. Its best to refer to your firewall documentation to find out how to add an exception.
Many of the topics I have covered today can also be found at the utorrent connection setup page.
Advanced topic: Change the maximum TCP/IP Connections per port. Refer to this great how-to on opening up the maximum number of TCP/IP connections in windows.
Part 1 Cont: Mac Torrent Client
Sorry Mac users I assumed utorrent was great for both Mac and PC but it looks like the Mac version of utorrent left out a few things. There is however a freely available program called Transmission is just as small and feature rich as utorrent for Windows.
Transmission has a few nice pluses that the Mac version of utorrent lacks such as rss feed support and selective file downloading for multi-part torrent files.
You can find transmission here: http://www.transmissionbt.com/index.php
Transmission has a few nice pluses that the Mac version of utorrent lacks such as rss feed support and selective file downloading for multi-part torrent files.
You can find transmission here: http://www.transmissionbt.com/index.php
Wednesday, January 27, 2010
Bittorrent Series Part 1 of 4: Choosing the right torrent client
I'll be writing a four part series this week that will address our favorite source for everything digital. Torrents! If your not already familiar with what a torrents are and how they work click here!
Torrents are a bit of a gray area when it comes to the theft of intellectual property and without going into a heated debate, I will say that this series is for educational purposes and warn users that unauthorized downloading of licensed software can lead to criminal investigation and up to a $250,000 fine.
Many of you have used torrents for years now and have settled on a bittorrent client that you feel pretty comfortable with. Though at some point you may have asked yourself "why is my computer running so slow when I'm downloading, how can I prevent my torrents from messing with my roommates internet speed, and whats all this talk about my torrent downloading being monitored?"
Whether your plagued by these issues or not, we all face the tedious task of searching for a virus free legitimate file that will offer optimal download speeds. Ill be addressing this equally troubling issue later in part 3.
Part 1: Choosing the right torrent client
When choosing a bittorrent client I follow 3 basic criteria:
Utorrent is a great torrent client out of the bunch. I've used it for a couple years now and it fits my requirements perfectly. Unlike torrent client programs such as Vuze and Bitcomet, Utorrent is a tiny 283kbs to download and offers all the same features in a easy to navigate layout that doesn't bombard you with a huge amount of information unless you tell it to.
You can find Utorrent here: http://www.utorrent.com/
After you download utorrent, here are a few little extras to keep you busy:
http://btjunkie.org/: Great search engine for hard to find torrents
http://www.demonoid.com/: great way to discover torrent files you may have never thought of.
http://www.entertane.com/: all your favorite torrent search engines in one place.
In my next post Ill guide you through an easy to follow step by step process of how to configure Utorrent to share bandwidth with others on your network and still give you fast download speeds. I'll also explain the importance of IP filters and how literally thousands of corporations and organizations may be monitoring your torrent activity at any given moment.
Torrents are a bit of a gray area when it comes to the theft of intellectual property and without going into a heated debate, I will say that this series is for educational purposes and warn users that unauthorized downloading of licensed software can lead to criminal investigation and up to a $250,000 fine.
Many of you have used torrents for years now and have settled on a bittorrent client that you feel pretty comfortable with. Though at some point you may have asked yourself "why is my computer running so slow when I'm downloading, how can I prevent my torrents from messing with my roommates internet speed, and whats all this talk about my torrent downloading being monitored?"
Whether your plagued by these issues or not, we all face the tedious task of searching for a virus free legitimate file that will offer optimal download speeds. Ill be addressing this equally troubling issue later in part 3.
Part 1: Choosing the right torrent client
When choosing a bittorrent client I follow 3 basic criteria:
- Is it small and does it consume the least amount of resources.
- Can I configure my torrent port usage and download speed.
- Does it have an IP Filter.
Utorrent is a great torrent client out of the bunch. I've used it for a couple years now and it fits my requirements perfectly. Unlike torrent client programs such as Vuze and Bitcomet, Utorrent is a tiny 283kbs to download and offers all the same features in a easy to navigate layout that doesn't bombard you with a huge amount of information unless you tell it to.
You can find Utorrent here: http://www.utorrent.com/
After you download utorrent, here are a few little extras to keep you busy:
http://btjunkie.org/: Great search engine for hard to find torrents
http://www.demonoid.com/: great way to discover torrent files you may have never thought of.
http://www.entertane.com/: all your favorite torrent search engines in one place.
In my next post Ill guide you through an easy to follow step by step process of how to configure Utorrent to share bandwidth with others on your network and still give you fast download speeds. I'll also explain the importance of IP filters and how literally thousands of corporations and organizations may be monitoring your torrent activity at any given moment.
Monday, January 25, 2010
Resizing images made easy
If your like me you end up with hundreds if not thousands of photos from a day of shooting and now face the tedious task of organizing, editing, and resizing your photos. While photo software suites help with performing batch resizing jobs you often need to pay an arm and a leg for quality software which often presents you with the tedious task of getting it to do what you want it to do.
If your looking for a quick way to resize a large amount of images to reduce the overall disk space your pictures are taking up you can use a great free utility called Mihov's Image resizer. This tool lets you resize .jpg, .gif, .bmp formats as well as perform several types of picture conversions.
You can download Mihov Image resizer @ http://www.imageresizer.com/
When you first install the program be sure to take a peek at the options section. There you can specify the way Mihov saves your new images either by appending a new file name or saving to a new folder.
There are also services such as Photobucket.com that let you upload your images an online account. This is a great way to store backups of your photos as well. You can also specify if you would like to have these images automatically resized upon upload.
If your looking for a quick way to resize a large amount of images to reduce the overall disk space your pictures are taking up you can use a great free utility called Mihov's Image resizer. This tool lets you resize .jpg, .gif, .bmp formats as well as perform several types of picture conversions.
You can download Mihov Image resizer @ http://www.imageresizer.com/
When you first install the program be sure to take a peek at the options section. There you can specify the way Mihov saves your new images either by appending a new file name or saving to a new folder.
There are also services such as Photobucket.com that let you upload your images an online account. This is a great way to store backups of your photos as well. You can also specify if you would like to have these images automatically resized upon upload.
How to create your own windows shortcut keys
There's an old saying I like to tell people when they start experiencing computer frustrations. Computers can improve efficiency by 300% but often create 100% more work. In other words, you can improve your work output tremendously but you might go a little crazy trying to get there.
A technique essential to maximizing your work efficiency in a Windows or Mac OS environment is the use of keyboard shortcuts. Quick keys are keyboard shortcuts you can use to perform a simple task like copying and pasting, or opening a program like your favorite internet browser.
Complete list of Windows shortcuts
Complete list of Mac OS X shortcuts
Today I'd like to teach you how you can set your own keyboard shortcuts for programs you'd like to access the quickest way possible at the touch of a finger.
I use spybot a lot to perform all sorts of maintenance behind the scenes. So for this example, I'm going to assign a keyboard shortcut to access spybot.
First, locate the icon of the program you want to assign the shortcut. In this case spybot

Next, open the properties window by right-clicking the icon and select properties.

Now, define your shortcut key by clicking in the shortcut key field, then hold the ctrl key and press the key that you would like to use as your shortcut.

I choose to assign the "0" key to this shortcut since I know 0 is not a key I already use. Now all I have to do to open spybot is press Ctrl + Alt + 0. You may find that assigning keys that are close to the Ctrl and Alt keys are more efficient since you can use one hand to open the shortcut. It's good practice to use keys you can remember easily such as Ctrl + Alt + P to open windows Paint.
A technique essential to maximizing your work efficiency in a Windows or Mac OS environment is the use of keyboard shortcuts. Quick keys are keyboard shortcuts you can use to perform a simple task like copying and pasting, or opening a program like your favorite internet browser.
Complete list of Windows shortcuts
Complete list of Mac OS X shortcuts
Today I'd like to teach you how you can set your own keyboard shortcuts for programs you'd like to access the quickest way possible at the touch of a finger.
I use spybot a lot to perform all sorts of maintenance behind the scenes. So for this example, I'm going to assign a keyboard shortcut to access spybot.
First, locate the icon of the program you want to assign the shortcut. In this case spybot

Next, open the properties window by right-clicking the icon and select properties.

Now, define your shortcut key by clicking in the shortcut key field, then hold the ctrl key and press the key that you would like to use as your shortcut.

I choose to assign the "0" key to this shortcut since I know 0 is not a key I already use. Now all I have to do to open spybot is press Ctrl + Alt + 0. You may find that assigning keys that are close to the Ctrl and Alt keys are more efficient since you can use one hand to open the shortcut. It's good practice to use keys you can remember easily such as Ctrl + Alt + P to open windows Paint.
Sunday, January 24, 2010
Defraging your hard drive the right way
If you have ever owned a PC you know how essential it is to make defragmentation of your hard drive part of your monthly (or weekly) ritual. If not, a routinely scheduled defragmentation of your hard drive can do wonders for both the performance of your computer and the health of your hard drive. Defragging organizes the data on your hard drive and ultimately reduces the amount of work being done by mechanical parts within the drive.
Mac Users will be happy to know that OS X performs file defragmentation while your computer is idle. Very efficient. For many new PC owners, Windows Vista and Windows 7 now performs a scheduled defragmentation of your hard drive automatically.
Tech-Fu Tool: O&O Defrag is a great free tool I have found to be faster and more efficient than the default windows defragmentation utility. There are also some great additional features you can play with to further improve performance.
Click here to get your free version of O&O defrag professional.
This free version does require a valid email to receive your free user license. Once you register, you will be sent an email containing your free user license. Simply download and install O&O defrag professional then enter the information included in this email.
Enjoy!
Mac Users will be happy to know that OS X performs file defragmentation while your computer is idle. Very efficient. For many new PC owners, Windows Vista and Windows 7 now performs a scheduled defragmentation of your hard drive automatically.
Tech-Fu Tool: O&O Defrag is a great free tool I have found to be faster and more efficient than the default windows defragmentation utility. There are also some great additional features you can play with to further improve performance.
Click here to get your free version of O&O defrag professional.
This free version does require a valid email to receive your free user license. Once you register, you will be sent an email containing your free user license. Simply download and install O&O defrag professional then enter the information included in this email.
Enjoy!
Thursday, January 21, 2010
Cookies that stick around even after you clean your temp folder.
Cookies are the most common way websites track you and often cause a good deal of clutter on your system. I always inform customers to perform a regular cleaning of cookies and temporary internet files in their browser. Find out more about how cookies work , and how to remove them.
Today I found a great article from a technology blog called Cybernews that informs people of a specific type of cookie that sticks around even after doing thorough cleaning of cookies. They're called flash-cookies. You may have heard the term "flash" mentioned before. Basically, anytime you see animated or interactive portion of a website, that's flash hard at work. Many of these sites use flash-cookies providing them a sure fire way to keep their cookies in your browser and track your browsing progress.
Today I found a great article from a technology blog called Cybernews that informs people of a specific type of cookie that sticks around even after doing thorough cleaning of cookies. They're called flash-cookies. You may have heard the term "flash" mentioned before. Basically, anytime you see animated or interactive portion of a website, that's flash hard at work. Many of these sites use flash-cookies providing them a sure fire way to keep their cookies in your browser and track your browsing progress.
Wednesday, January 20, 2010
Great little tool for anonynimity against google.
I found a great little tool today that will help keep you anonymous on the web. If your a Firefox user your going to like this Firefox plug-in from security software developer Moxie Marlinspike. He's come up with a way to prevent google from tracking your internet statistics. His plug-in is called GoogleSharing. Not to be confused with "Google Sharing" which is a google product that allows you to share content with your gmail contacts.
What?! google tracks your every move!?
Google has long held the belief that to be an effective search engine it must track, catalog, and analyze every site you visit, terms you search for, and IP address's of your computer. All this information is used to track consumer and economic trends that aid hundreds of thousands if not millions of business's and corporations in market research. Here, see for your self with Google trends.
GoogleSharing
GoogleSharing is not a fully functioning proxy server(what is a proxy server?) but a proxy service specifically designed to reroute your web browser traffic interacting with google services to a GoogleSharing proxy server. Once there your personal information is stripped from your traffic and replaced with a GoogleSharing identity and sent off to google. If you'd like a full explanation of GoogleSharing please click here.
Downside
There is one downside that will eventually disappear as the plug-in undergoes more development. GoogleSharing is currently only available for Firefox: 3.0 – 3.5. This means if you have any other version of Firefox installed on your system you will not be able to use this plug-in.
Labels:
firefox plug-in,
google sharing,
google trends,
proxy,
proxy server
Sunday, January 17, 2010
A last attempt
The Scammer that tried to con me into cashing the checks he sent me made his final attempt today to solicit me. This is what he said:
Greetings to you,
I don't know what you are up to,with your sudden silence over the payment you received from our client,i mailed you several times but you never reply back,ifyou know that you are not ready to work you shouldn't have given down your details to the company and am sure you are aware of the fact that you can never abscond with the company's funds and if your intention is to made away with the company's fund,you will face the penalty and will be sue to court. So i will urge you to get back to me within 48 hours if only you don't want to face the penalty,your response is needed urgently concerning this payment and I need you to get back to me as soon as possible.I will await your urgent response within 48 hours or else your details will be forward to the FBI and I can bet it.
Can you believe this guy. I informed him that I have contacted several internet fraud Organizations, and Starlight Children's Foundation concerning his recent activity. But as you can see, the grammar inconsistencies and spelling errors were enough to know English was not this person's first language. A bit suspicious for a founder of a british charity.
Scammers are usually Cowards.
My first question to John Weston, Moderator for the internet fraud advisory group Data Wales, was whether or not these individuals are prone to tracking people down and harassing them physically. His answer was a resounding no. These scammers will try to remain as anonymous as possible. All interaction they have with the internet is done so at coffee shops and internet cafe's keeping their connection as "off-the-grid" as possible. Once they decide your no longer an easy target, they cut all contact and move on to the next person.
So you caught em with your awesome tech fu right?
Through the course of this encounter, the techniques I've used have not yielded enough information to track down this Scammer. In addition to email, I've also received text messages from a phoney number which I cannot trace or track.
Where is the justice then?
You can now see how these individuals have an easy time convincing others to unwittingly commit crime for them and remain annonymous enough to move to a new location and start over. Internet Fraud Organizations are unable to rely on the evidence collected from just one incident. Investigators will look for patterns amoungst multiple incidents and coordinate their efforts with other agentcies to determine the best course of action. The more incidents they have on record the closer they get to catching the culprit. Unfortunately, the damage these criminals leave behind cannot be undone.
Greetings to you,
I don't know what you are up to,with your sudden silence over the payment you received from our client,i mailed you several times but you never reply back,ifyou know that you are not ready to work you shouldn't have given down your details to the company and am sure you are aware of the fact that you can never abscond with the company's funds and if your intention is to made away with the company's fund,you will face the penalty and will be sue to court. So i will urge you to get back to me within 48 hours if only you don't want to face the penalty,your response is needed urgently concerning this payment and I need you to get back to me as soon as possible.I will await your urgent response within 48 hours or else your details will be forward to the FBI and I can bet it.
Can you believe this guy. I informed him that I have contacted several internet fraud Organizations, and Starlight Children's Foundation concerning his recent activity. But as you can see, the grammar inconsistencies and spelling errors were enough to know English was not this person's first language. A bit suspicious for a founder of a british charity.
Scammers are usually Cowards.
My first question to John Weston, Moderator for the internet fraud advisory group Data Wales, was whether or not these individuals are prone to tracking people down and harassing them physically. His answer was a resounding no. These scammers will try to remain as anonymous as possible. All interaction they have with the internet is done so at coffee shops and internet cafe's keeping their connection as "off-the-grid" as possible. Once they decide your no longer an easy target, they cut all contact and move on to the next person.
So you caught em with your awesome tech fu right?
Through the course of this encounter, the techniques I've used have not yielded enough information to track down this Scammer. In addition to email, I've also received text messages from a phoney number which I cannot trace or track.
Where is the justice then?
You can now see how these individuals have an easy time convincing others to unwittingly commit crime for them and remain annonymous enough to move to a new location and start over. Internet Fraud Organizations are unable to rely on the evidence collected from just one incident. Investigators will look for patterns amoungst multiple incidents and coordinate their efforts with other agentcies to determine the best course of action. The more incidents they have on record the closer they get to catching the culprit. Unfortunately, the damage these criminals leave behind cannot be undone.
Subscribe to:
Comments (Atom)
