A great thing I've always loved about P2P file sharing is the active and necessary role people play to create an infrastructure of freely available content. No knowledge of how P2P works is necessary to benefit from its availability. By uploading your own torrents you take an active role in the free distribution of information. Torrents are not always comprised of pirated software and illegal movies. They can be custom compilations of your favorite freeware programs, a film you recently produced you'd like to distribute, or old books you recently converted to pdf's. Whatever it may be you can torrent just about anything. If your looking to upload an extremely popular torrent, a "public torrent" is ideal for you.
Step 1: Account Setup
First, you will need to create an account with a torrent search engine. In this tutorial were going to use Utorrent as our torrent client of choice, and btjunkie.org as our torrent search engine.
To do this, go to btjunkie.org and click the member link:

Next, click the sign up link:

You will be taken to the account creation page:

You will need a vaild email address for this. You will be sent an email verification. In that email, you will need to click the "verify account" link. Now your ready to begin uploading torrents.
Step 2: Creating your first torrent file
Before we move on, I'd like to take a second to explain how this next part works. If you already understand how torrent metadata works then skip this explanation. I'm going to refer back to my analogy I used in Part 2 where I associated computers and internet connections as businesses connected by roads and freeways. Think of a torrent file as an informational roadsign along one of these roadways. This sign will guide people to your store. When you create a "torrent" file, what your doing is setting up a roadsign that tells others several important pieces of information:
1) Where the computer or server containing the file is located.
2) Where the file is located on said computer or server.
3) What torrent tracking servers will be paying attention to this file.
4) Is this torrent private or is it public.
So again, a torrent is not the actual file you are sharing. It is a file containing the information a torrent client will need to locate desired data as it exists on one or multiple computers. In this case, since you are creating a torrent to share a file on your computer, you will be the sole owner of that file until another person completes a download of your file. They will then become a "seeder" of that file and begin uploading in the same way you are.
So lets begin shall we...
Open Utorrent, click the "File" menu, then click "Create New Torrent" from the drop down menu. You can also do this by using the hotkey "Ctrl + N" :

Don't be intimidated by the next window:

This is where we actually create our roadsign. Since we are creating a basic public torrent file we only need to follow 4 steps:
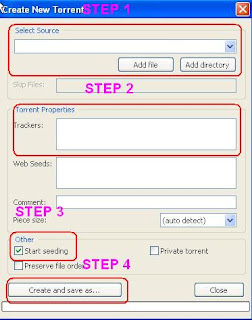
Step 1
Locate the file or folder you want to share with others by clicking the "add file" or "add directory" button. This can be a compressed archive like a zip file or rar file, program executable, movie, anything. I have a collection of great PC technician tools I'd like to share with others that I've compressed into a single rar file.
Step 2
This part can be a little tricky for some. We're going to add a tracker server address for your torrent. . A torrent server address looks like any other website address (http://blah.com:80) with a port number appended to it. I've included a short list of working torrent tracker addresses you can use to get you started. Simply copy and paste one or more of the addresses found below into the the step 2 box shown above. Be sure there is a space separating each address or utorrent will not recognize the address:
http://denis.stalker.h3q.com:6969/announce
http://tpb.tracker.prq.to/announce
http://tracker.prq.to/announce
http://tracker.torrent.to:2710/announce
http://tv.tracker.prq.to/announce
*SPEED BOOST TIP: If your downloading a torrent with a low amount of seeders you can add more by adding additional tracker addresses to the torrent file to give you a possible boost in speed. Simply right click on your download and go to properties. There you will find the tracker server list which you can modify by adding any number of tracker address.
Step 3
Ensure that the "Start Seeding" check box is filled. This will start seeding your torrent the moment it's created.
Step 4
Now your done. You can click "Create torrent" and save it as a descriptive file name that will help tell people what your torrent is. Since this is not the title people will see when they search for your torrent there's no need to include a large file name.
Step 3: Make your torrent available to others
Just a quick note. If you'd like to share your torrent with a small group of friends rather than make it available to anyone able to search btjunkie, you can email the torrent you just created to a friend. Once they receive the torrent they can begin downloading your file immediately. For those familiar with FTP services this feature could serve as an alternative in some situations.
Let's go back to btjunkie.org and login to your account by going to the members section then enter your username and password. Once logged in, the upload feature will be available to you:


Click upload and you will be taken to the upload page:

Step 1
Click browse and navigate to the torrent you just created.
Step 2
Create a label for your torrent that search engines will use to identify your torrent. It helps to make your description long containing keywords that may help your torrent show up in more searches. For example, I called my file "Great PC utilities Memtest 0&O defrag Anti-Malware". If someone searches for any of these terms my file will show up in their search.
Step 3
Select the Category you'd like your torrent to fall under. This helps users find your torrent easier when they refine a search to include a specific category.
Your almost done. Enter a Capcha then scroll dow and click the verification bubble, then hit upload. After the upload completes you should see something like this:

And thats it. After a few hours or so your search will eventually start showing up in btjunkie.org.
Conclusion
If you have read all 4 parts of my Bittorrent series, you should have a much better understanding for how torrents work and how to utilize them as a valuable resource. I recommend doing your own research on torrents since the topics I wasn't able to cover in this tutorial are NUMEROUS!
Torrents are merely the latest evolution in P2P file sharing. It's hard to say what direction the free distribution of information will take in the coming decade but its very exciting to know it can only get better from here. The file sharing provides some valuable tools for learning which no individual should be restricted from or hindered by.